PWNABLE-collision
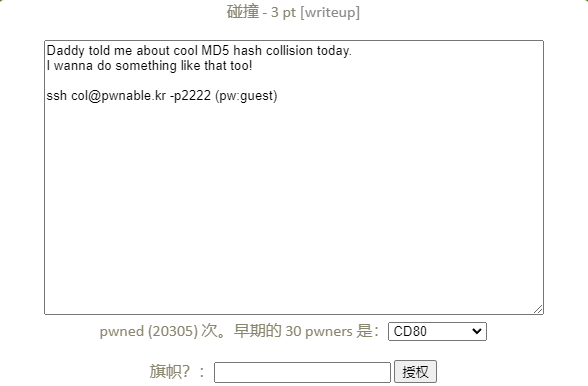
题目信息
源码分析
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
| #include <stdio.h>
#include <string.h>
unsigned long hashcode = 0x21DD09EC;
unsigned long check_password(const char* p){
int* ip = (int*)p;
int i;
int res=0;
for(i=0; i<5; i++){
res += ip[i];
}
return res;
}
int main(int argc, char* argv[]){
if(argc<2){
printf("usage : %s [passcode]\n", argv[0]);
return 0;
}
if(strlen(argv[1]) != 20){
printf("passcode length should be 20 bytes\n");
return 0;
}
if(hashcode == check_password( argv[1] )){
system("/bin/cat flag");
return 0;
}
else
printf("wrong passcode.\n");
return 0;
}
|
不难看出只要让hashcode == check_password( argv[1] )成立,就可以拿到flag
题目要求输入的是20位的串,而char转换为int就是每四位换成一个int型,那么就可以把这20位分成五组
0x21DD09EC --> 568134124
568134124 = 113626824 * 4 + 113626828
113626824 --> 0x6c5cec8
113626828 --> 0x6c5cecc
EXP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| from pwn import *
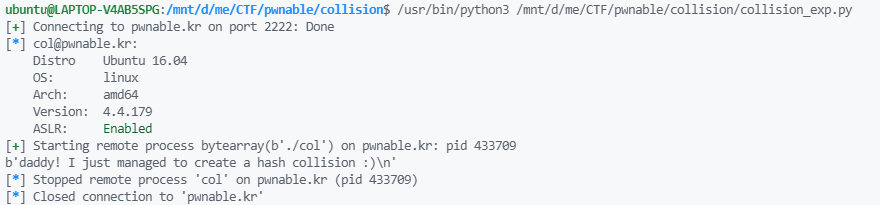
p = ssh('col', 'pwnable.kr', password='guest', port=2222)
payload = p32(0x6c5cec8) * 4 + p32(0x6c5cecc)
pr = p.process(executable='./col', argv=['col', payload])
flag = pr.recv()
print(flag)
pr.close()
p.close()
|
结果