BUUCTF-PWN-jarvisoj_level2
BUUCTF-PWN-jarvisoj_level2
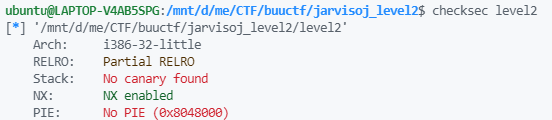
checksec
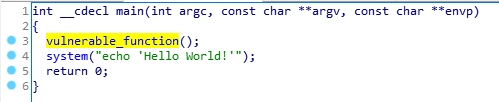
IDA
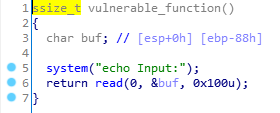
read是一个溢出点
查看字符串,发现有binsh
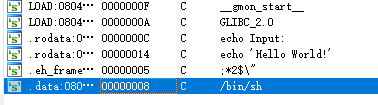
找到binsh地址

再找到system在text段的地址
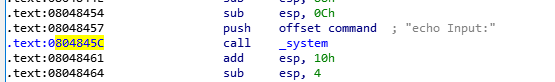
EXP
1 | from pwn import * |
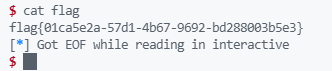
结果
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Clerk.Max(well);!
评论



read是一个溢出点
查看字符串,发现有binsh

找到binsh地址

再找到system在text段的地址

1 | from pwn import * |
