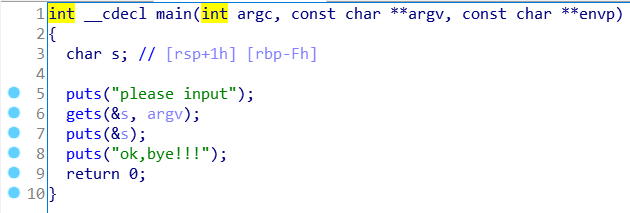
BUUCTF-PWN-not_the_same_3dsctf_2016
BUUCTF-PWN-not_the_same_3dsctf_2016
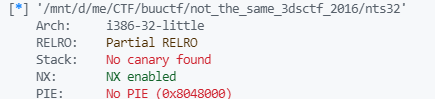
checksec
IDA
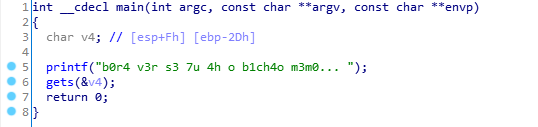
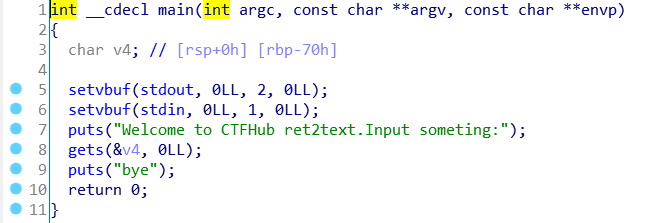
main函数中的gets函数可以溢出
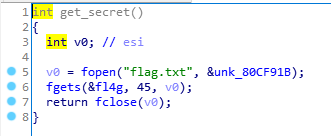
这个函数读取了flag,并存入到变量fl4g中,且其在bss段,如下图:
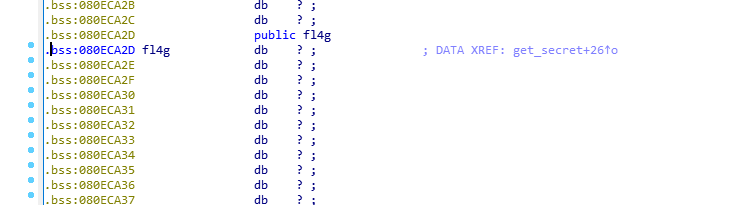
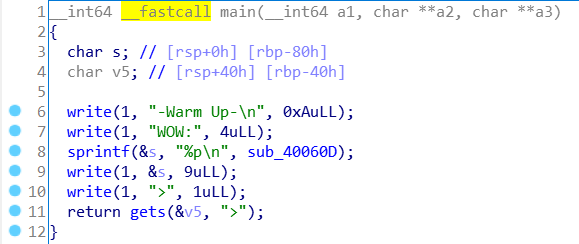
那么我们只需要使get_secret()函数运行,然后再利用write函数将flag写出就行了
EXP
1 | from pwn import * |
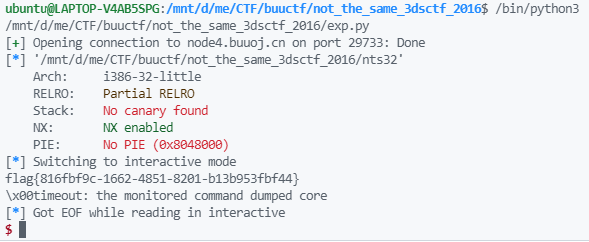
结果
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Clerk.Max(well);!
评论